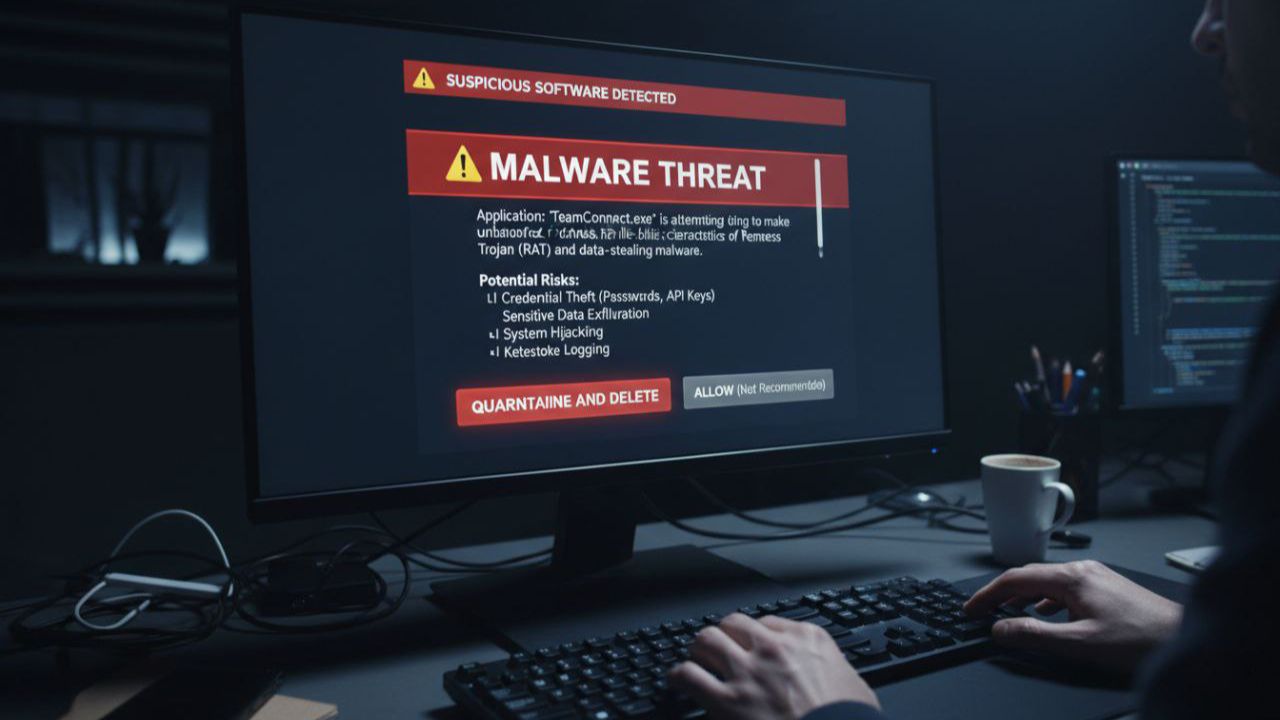
I Just Read About a Developer Who Nearly Got Hacked Through a Fake Job Interview – And Here’s Proof It’s Still Happening
So I came across this blog post about a freelance developer who almost ran malware during what looked like a legitimate job interview. The story stuck with me because it shows how sophisticated these scams have become – and based on what I’m seeing in the comments and LinkedIn conversations, multiple people have already fallen victim to this exact attack.
Here’s what happened: The guy got a LinkedIn message from someone claiming to be a Chief Blockchain Officer at Symfa (which is a real company). The profile looked legit – 1,000+ connections, professional details, the whole package. They were recruiting for a blockchain project and sent him a coding challenge before the interview. Standard practice, right?
He was running late and only had 30 minutes to review the code before their call. Instead of his usual routine of sandboxing everything in Docker, he rushed. He spent those 30 minutes fixing bugs and cleaning up the code, getting ready to run it.
Then – and this is the part that saved him – he had a moment of paranoia. Right before executing npm start, he asked his AI coding assistant to scan the codebase for anything suspicious. Turns out the code was packed with malware designed to access environment variables, database credentials, crypto wallets, and file systems. Everything a server-side Node.js application can access.
What These Scam Messages Actually Look Like
Here’s where it gets really interesting. I found a screenshot of an actual conversation between someone (Bozidar Zecevic) and one of these scammers posing as “Daniel Sanderson”:
Initially, Bozidar (with a verified checkmark) asks: “Hi Daniel, repo is not available anymore, what happened?”
Then the scammer (Daniel Sanderson) responds with an incredibly professional message:
“sorry, this test is not available anymore.
you should have a project review
Please conduct a comprehensive review of the project’s components, available at the following link: https://github.com/Dex-MVP-v1/Dex-platform
Your review should focus on the following aspects:
– User Experience and Design Flexibility: Evaluate the intuitiveness, responsiveness, and overall usability of the interface.
– Core Functionality: Ensure that key functions, such as token swapping, wallet connection, and transaction history, function as expected.
– Component Architecture and Efficiency: Evaluate the modularity, clarity, and efficiency of component design.
– Timeline: 2hrs.Please carefully review these aspects to ensure the project is accessible and functional within the applicant’s environment.
When you finish it, please send your feedback as a PDF file with screenshots.”
Look at How Convincing This Is:
- Professional language and structure
- Specific technical evaluation criteria
- Legitimate-sounding project (DEX platform – decentralized exchange)
- The focus on crypto functionality (token swapping, wallet connection) – perfect bait for developers
- 2-hour timeline creating subtle pressure
- Request for detailed feedback with screenshots
- GitHub link that looks professional
But here’s the brilliant part – Bozidar was smart. When the scammer (Daniel Sanderson) followed up asking “Hi, are you still interested for this position?”, Bozidar replied:
“I am but repo looks suspicious so I am not going to run it, sorry
A lot of malicious repos are shared around the network and your profile doesn’t give much confidence to be honest”
The scammer’s response? “Make sense. Thanks for your time”
And then Bozidar’s final reply: “Haha, sure”
That exchange shows someone who trusted their instincts. A real recruiter would be concerned about their repo being flagged as suspicious and would offer to verify their identity or use official company channels. Instead, the scammer just moves on to the next target.
What the Malware Actually Does (From People Who Weren’t So Lucky)
According to victims in the comments, this isn’t just theoretical – people have been hit hard:
- Crypto wallet devastation: The script breaks through MetaMask passwords and completely drains wallets
- Browser password manager breach: It extracts everything from your browser’s saved passwords using some kind of brutal brute force attack that works within an hour
- Account theft: Victims reported losing access to Netflix and other subscription accounts
- Remote access installation: The malware pulls in Python scripts that install AnyDesk, giving attackers persistent remote access to your machine
The Docker Myth
Here’s something that surprised me – one commenter pointed out that running this in Docker doesn’t guarantee safety. I always thought Docker isolation would protect against this kind of attack, but apparently these scripts are sophisticated enough to break out or the damage happens before you realize what’s running.
Red Flags to Watch For (Based on the Real Conversation)
Looking at that screenshot, here are the warning signs:
- Bait and switch: The original “test” suddenly becomes a comprehensive 2-hour project review
- Time pressure: 2-hour deadline for a “comprehensive review”
- Crypto focus: Any coding challenge heavily focused on wallet connections and token swapping should raise eyebrows
- Profile inconsistencies: Bozidar noted the profile “doesn’t give much confidence” – always verify through official company channels
- GitHub repo structure: Check if the organization/user has other legitimate projects
- PDF deliverable request: Asking for screenshots and PDF feedback could be harvesting information about your environment
- Casual response when questioned: Moving on quickly instead of professional concern
The Bigger Picture
The attack vector is brilliant (in a terrifying way). Developers download and run code constantly – GitHub repos, npm packages, coding challenges. We don’t sandbox everything, especially when we’re in a rush. This was server-side malware with full Node.js privileges, targeting exactly the kind of people who have production credentials and sensitive data on their machines.
The LinkedIn profiles aren’t just throwaway fake accounts. These scammers clone real companies’ branding, create convincing profiles with verified checkmarks, and craft professional-sounding messages. Based on the reports, this appears to be an active, ongoing campaign with multiple victims.
What You Should Do Right Now
- Never run unfamiliar code on your main machine – Even Docker isn’t foolproof
- Verify the person independently – Don’t just trust the LinkedIn profile messaging you. Go to the actual company website and verify
- Be suspicious of time pressure or paycheck – Legitimate companies don’t need you to complete a comprehensive review in 2 hours, and $120/hour rate, hmmm…
- Check the GitHub organization – Does it have other legitimate projects? When was it created? Does it match the company’s real GitHub?
- If it involves crypto, be extra paranoid – Wallet connections and token swapping in a “test project” is a massive red flag
- Run security scans before executing anything – Use AI assistants, static analysis tools, or manual code review to check for suspicious patterns
- Trust your gut – If something feels off, it probably is
The Lesson
This isn’t about being smarter or more careful. These scams are sophisticated enough to fool security professionals. The original developer who almost got hacked was paranoid about security and had 8 years of freelancing experience. Daniel in the screenshot was smart enough to question the repo.
The real lesson is that we need to slow down and verify, even when things look legitimate. The fact that multiple people have already lost their crypto wallets, passwords, and accounts to this exact scam shows it’s not just a hypothetical threat.
Stay safe out there, and if you get a LinkedIn message about a coding challenge involving crypto functionality – think twice, check thrice.
Sources:
- Original Blog Post: “How I Almost Got Hacked By A ‘Job Interview'” by David Dodda
https://blog.daviddodda.com/how-i-almost-got-hacked-by-a-job-interview - Hacker News Discussion: Community discussion with additional victim reports and technical analysis
https://news.ycombinator.com/item?id=45591707 - Related Security Research: “I’m a security expert and I almost fell for this IT job scam” – The Register
https://www.theregister.com/2025/02/11/it_worker_scam - In-Depth Analysis: “AI fakers exposed in tech dev recruitment: postmortem” – Pragmatic Engineer
https://newsletter.pragmaticengineer.com/p/ai-fakers - Community Discussion: Lobsters thread with additional security perspectives
https://lobste.rs/s/zfelwy/how_i_almost_got_hacked_by_job_interview
Share and subscribe to our newsletter.